Enhanced Security: GRIP includes an enhanced system security. Each group of information and function is assigned a resource permission. These resource permissions can either be assigned to a group or an individual. If a user does not have a specific resource permission, either directly assigned or via membership in a group, they are restricted from viewing/editing data or performing secure functions. For example, a user may be granted permission to view data records, but may not be able to edit those records. Security is completely and totally controlled by an on-site systems administrator.
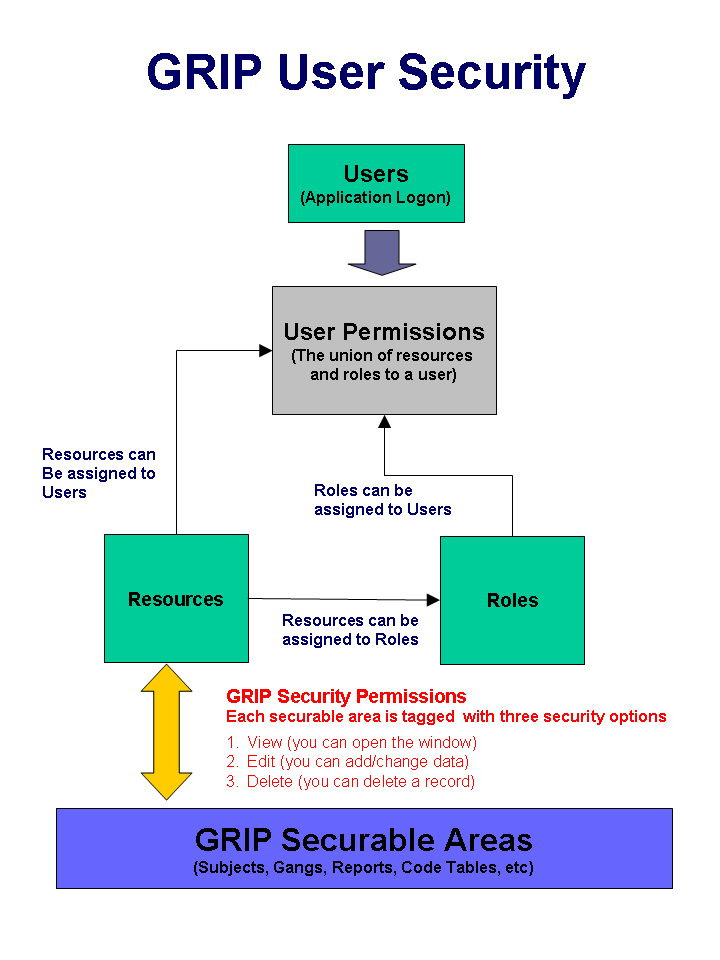
GRIP® Security is composed of three components, resources, roles and users.
Resources are tags assigned to each window and/or function in GRIP®. Each securable area in the program has edit, view and delete permissions. If a user is associated with a resource tag, they are able to access or edit the relevant data. For example, if a user is associated with the subject_view resource tag, they can view subjects. Resource tags are defined by DB Software Associates.
Roles are collections of resources. The security administrator can create new or modify existing roles. A role allows a collection of resources to be associated together for easier security administration. For example, a viewer role can be created and all resources that allow viewing can be associated to it. This role can then be assigned to individual users
Users are individual users of the GRIP® application. A user can either be assigned one or more roles and/or one or more individual resources. The user will have the cumulative permissions of all assigned roles and resources. When defining a user, the administrator must assign a user id (to be used when logging in), a default password of ‘password’ is initially assigned, a user first name, a user last name, and a user description. Once defined, the administrator can assign roles and resources.
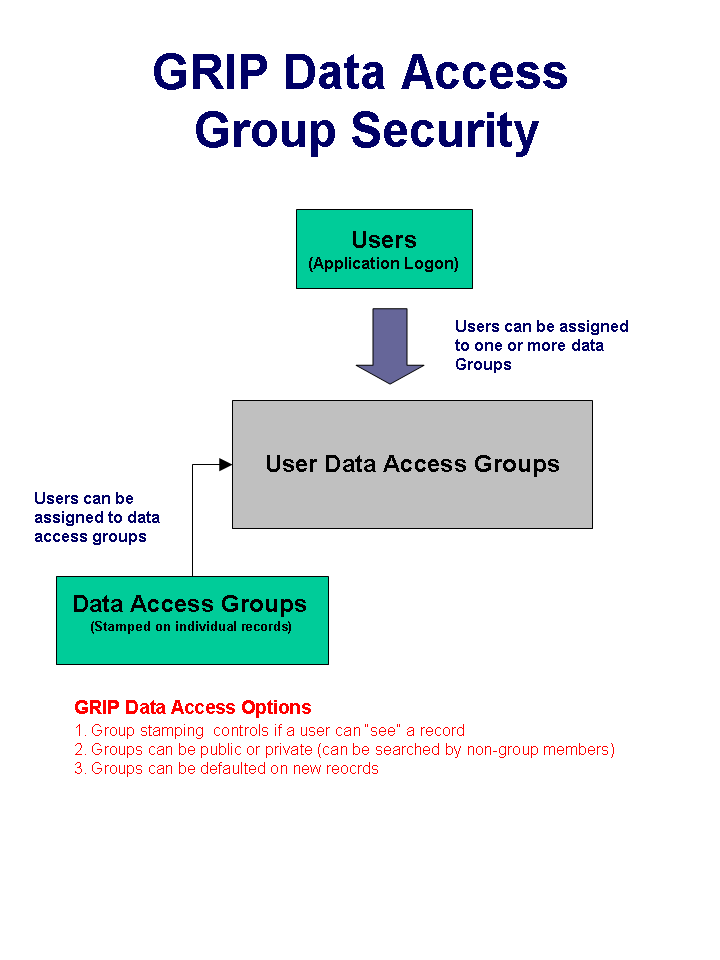
GRIP has the ability to restrict access to records by including or excluding users from security Data Access Groups. Data Access Groups are a grouping of like users who are allowed the view details of marked records. The following modules support data access groups:
When entering a record in GRIP, users are allowed to select a Security Group (Data Access Group) that is associated to it. From that point forward, only members of the Security Group are allowed to view or edit the details of the record. Depending on configurable settings, others users may or may not be informed about the existence of the record by the system when searching.